6. Keys for the SAS-RCS/RBS
by: saaiqSAS
Last Updated: 27/2/2025
The SAS-RCS/RBS Encryption Algorithms are built on the foundation of the SAS-ROS Cipher
and utilize the same two types of keys: Dynamic Key and Static Key.
However, unlike the ROS Cipher, the SAS-RCS/RBS Dynamic Key incorporates additional
components, and multiple Static Keys are employed instead of just one.
In addition to the core encryption mechanism, the SAS-RCS/RBS algorithms include extra cryptographic
steps such as obfuscation and shuffling. The unique information required for these steps is stored
in the initial section (settings) of the Dynamic Key as integers. This section contains
a total of 10 such integers. The latter part of the Dynamic Key, referred to as the
Charset, stores the object array (ROS Cipher Dynamic Key) used for the ROS process.
Fig. 6.1 illustrates the structure of the SAS-RCS/RBS Dynamic Key.
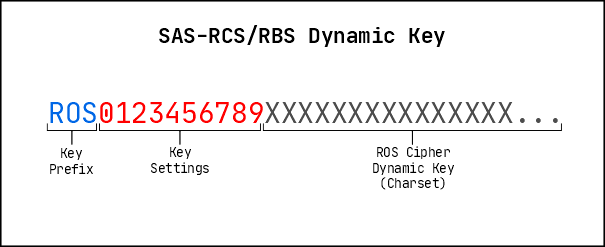 Fig.6.1
Example 6.1: 128 char (7 bit) String Dynamic Key generated from the SAS-ROSET API v1.0.0
ROSDK:0213030201lNh+¸e^`¤aBQF&u\9TÀKwm°Z>S*¢² =$/U06_¬¨L ¾]§gº(~jsO;,PV<8?nxAdz-¿·kJ¯#to4b)»±"«EH¡@¼}|qW¶¹D¥v{Y£c´.2G!Xª½Mf¦51rpR'i3[©:y7%®I³µC
The Static Key in SAS-RCS/RBS is identical to that of the ROS Cipher.
In addition to being used for the ROS process, the Static Keys are also
employed in the shuffling step of SAS-RCS/RBS as a source of random numbers.
The SAS-ROSET API represents the Static Key as an int[] array of indexes (positions).
Example 6.2: 128 char (7 bit) int[] Static Key generated from the SAS-ROSET API v1.0.0
[90, 96, 118, 111, 81, 13, 88, 47, 98, 104, 0, 21, 33, 37, 30, 112, 85, 55, 89, 32, 113, 87, 49, 94, 43, 80, 93, 70, 36, 25, 116, 121, 31, 27, 22, 48, 71, 57, 73, 72, 101, 91, 10, 95, 126, 124, 68, 106, 75, 76, 127, 60, 107, 16, 29, 40, 61, 53, 34, 44, 125, 6, 11, 28, 119, 5, 26, 42, 4, 3, 46, 109, 86, 24, 123, 117, 83, 100, 99, 17, 8, 74, 77, 105, 38, 69, 103, 64, 2, 50, 122, 9, 7, 15, 35, 59, 12, 23, 14, 110, 19, 52, 45, 108, 65, 20, 67, 62, 18, 51, 58, 78, 102, 79, 41, 54, 114, 66, 115, 120, 56, 82, 92, 63, 1, 39, 97, 84]
Dynamic Key Settings
The following list provides a brief description of what each setting index (on Fig.6.1) represents along with the accepted values.
0 → ROS Method (0: m1, 1: m2)
1 → Static Key reversing order (min 0, max 3)
2 → RGM Status for text (0: disable, 1: partial, 2: full) [RCS Only]
3 → RGM Base (0: base2, 1: base10, 2: base16, 3: base64) [RCS Only]
4 → Empty
5 → Data Size Increase: For Every (min 0, max 9)
6 → Data Size Increase: Add - Tenths (min 0, max 9)
7 → Data Size Increase: Add - Units (min 0, max 9)
8 → Empty
9 → API Version ID
0. ROS Method: This index specifies the ROS method to use in encryption—either Method 1 or Method 2.
[Details on the methods for the ROS Cipher can be found in Section 1 - SAS-ROS Cipher]
Fig.6.1
Example 6.1: 128 char (7 bit) String Dynamic Key generated from the SAS-ROSET API v1.0.0
ROSDK:0213030201lNh+¸e^`¤aBQF&u\9TÀKwm°Z>S*¢² =$/U06_¬¨L ¾]§gº(~jsO;,PV<8?nxAdz-¿·kJ¯#to4b)»±"«EH¡@¼}|qW¶¹D¥v{Y£c´.2G!Xª½Mf¦51rpR'i3[©:y7%®I³µC
The Static Key in SAS-RCS/RBS is identical to that of the ROS Cipher.
In addition to being used for the ROS process, the Static Keys are also
employed in the shuffling step of SAS-RCS/RBS as a source of random numbers.
The SAS-ROSET API represents the Static Key as an int[] array of indexes (positions).
Example 6.2: 128 char (7 bit) int[] Static Key generated from the SAS-ROSET API v1.0.0
[90, 96, 118, 111, 81, 13, 88, 47, 98, 104, 0, 21, 33, 37, 30, 112, 85, 55, 89, 32, 113, 87, 49, 94, 43, 80, 93, 70, 36, 25, 116, 121, 31, 27, 22, 48, 71, 57, 73, 72, 101, 91, 10, 95, 126, 124, 68, 106, 75, 76, 127, 60, 107, 16, 29, 40, 61, 53, 34, 44, 125, 6, 11, 28, 119, 5, 26, 42, 4, 3, 46, 109, 86, 24, 123, 117, 83, 100, 99, 17, 8, 74, 77, 105, 38, 69, 103, 64, 2, 50, 122, 9, 7, 15, 35, 59, 12, 23, 14, 110, 19, 52, 45, 108, 65, 20, 67, 62, 18, 51, 58, 78, 102, 79, 41, 54, 114, 66, 115, 120, 56, 82, 92, 63, 1, 39, 97, 84]
Dynamic Key Settings
The following list provides a brief description of what each setting index (on Fig.6.1) represents along with the accepted values.
0 → ROS Method (0: m1, 1: m2)
1 → Static Key reversing order (min 0, max 3)
2 → RGM Status for text (0: disable, 1: partial, 2: full) [RCS Only]
3 → RGM Base (0: base2, 1: base10, 2: base16, 3: base64) [RCS Only]
4 → Empty
5 → Data Size Increase: For Every (min 0, max 9)
6 → Data Size Increase: Add - Tenths (min 0, max 9)
7 → Data Size Increase: Add - Units (min 0, max 9)
8 → Empty
9 → API Version ID
0. ROS Method: This index specifies the ROS method to use in encryption—either Method 1 or Method 2.
[Details on the methods for the ROS Cipher can be found in Section 1 - SAS-ROS Cipher]
1. Static Key Reversing Order: The SAS-RCS/RBS algorithm creates additional Static Keys in memory
by reversing certain Static Keys from the provided set. By default, half of the Static Keys will be
reversed and used as standalone Static Keys during processing. For example, if six Static Keys are
provided, the data will be processed with nine Static Keys (six original + three reversed). The "reversing order"
determines the starting Static Key and the direction in the provided list from which each Static Key will
be reversed until half of them are reversed.
2. RGM Status: The SAS-RGM algorithm is used in SAS-RCS to represent characters not found in the Dynamic Key
in terms of the characters within the Dynamic Key. The "RGM Status" value determines whether this feature is enabled
and to what extent it is used. It can be enabled partially, fully, or disabled. Disabling is not recommended. The "Full" status
processes all data characters (not limited to only external characters) through the RGM algorithm, while "Partial" status only
processes the required characters. Note that the output size of RGM for a single character will be large and varies depending
on the RGM Base used.
[Details on the SAS-RGM algorithm can be found in Section 7 - SAS-RGM: Random Group Mapping]
3. RGM Base: The SAS-RGM first converts characters to their base values (e.g., binary, hex) before processing. The
"RGM Base" determines which base to use in this step—either base2, base10, base16, or base64. Smaller bases result in larger output
sizes but provide more randomness to the output. Larger bases are better suited for use with larger keys.
5. Data Size Increase: For Every: This value represents the 'n' value in the ratio n:m.
6,7. Data Size Increase: Add: These values represent the 'm' value in the ratio n:m.
9. API Version ID: This value contains the X value of the API version in the format vX.Y.Z.
It may change after an update to the algorithm or the implementation (API), making the updated version non-backwards
compatible with older versions.
Keyspace
The effective keyspace for the ROS Cipher is the factorial of the key length (L!), representing the Sub-Space.
[Details on the keyspace for the ROS Cipher can be found in Section 2 - Keys for the SAS-ROS Cipher].
This keyspace applies to a single pair of keys (Dynamic Key and Static Key) that form a substitution table.
The SAS-RCS/RBS uses multiple Static Keys paired with a single Dynamic Key, resulting in multiple substitution tables.
To determine the effective keyspace for the SAS-RCS/RBS, multiply the effective keyspace for each pair. This is expressed as (L!)^number_of_st_keys.
However, this keyspace is not complete, as the SAS-RCS/RBS includes additional steps (settings). The keyspace for these settings is determined by the product of the maximum values for each individual setting. For example, 2 * 4 * 3 * 3 * 2 * 9 * 99 = 128304.
The accurate effective keyspace is the product of the settings keyspace and the previously calculated keyspace. This is expressed as ((L!)^number_of_st_keys) * 128304.

